Phishing Simulations
ATTACK Simulator's Practical StrategyOur phishing simulations transpose employees directly into the challenging battlefield of online cyberattacks. With ATTACK Simulator, the sole consequence of a successful phishing attack is learning and improvement.
Thinking that you can’t be the target of a cyberattack is fulfilling a hackers’ strongest desire: catching you off-guard. As long as there’s a financial gain, any company can become the victim of a costly cyberattack.
Don’t wait until they take the bait!
Security crises usually involve financial losses and slow recoveries, which might disrupt your business. Ongoing training is the safest way of protection against sophisticated attacks, and it starts with giving your employees empirical knowledge about security.
We design our simulations based on a core principle: understanding the hacker’s minds and anticipating their actions. Employees will be exposed to real-life simulations meant to stimulate them to develop defensive mechanisms aided by our targeted educational alerts.
SMBs targeted by phishing attacks
Average cost of a data breach
Average time to recover from cyberattacks
SMBs Close Within 6 Months Of Being Hacked
*according to a professional phishing report
Our Phishing Simulations are packed full of neat features
Automated attack simulation emails
Malware file replicas
Loyal to our promise for true-to-life attack simulations, we enhance emails with malware file replicas.
Real-life attack scenarios
Interactive lessons
User behavior analysis
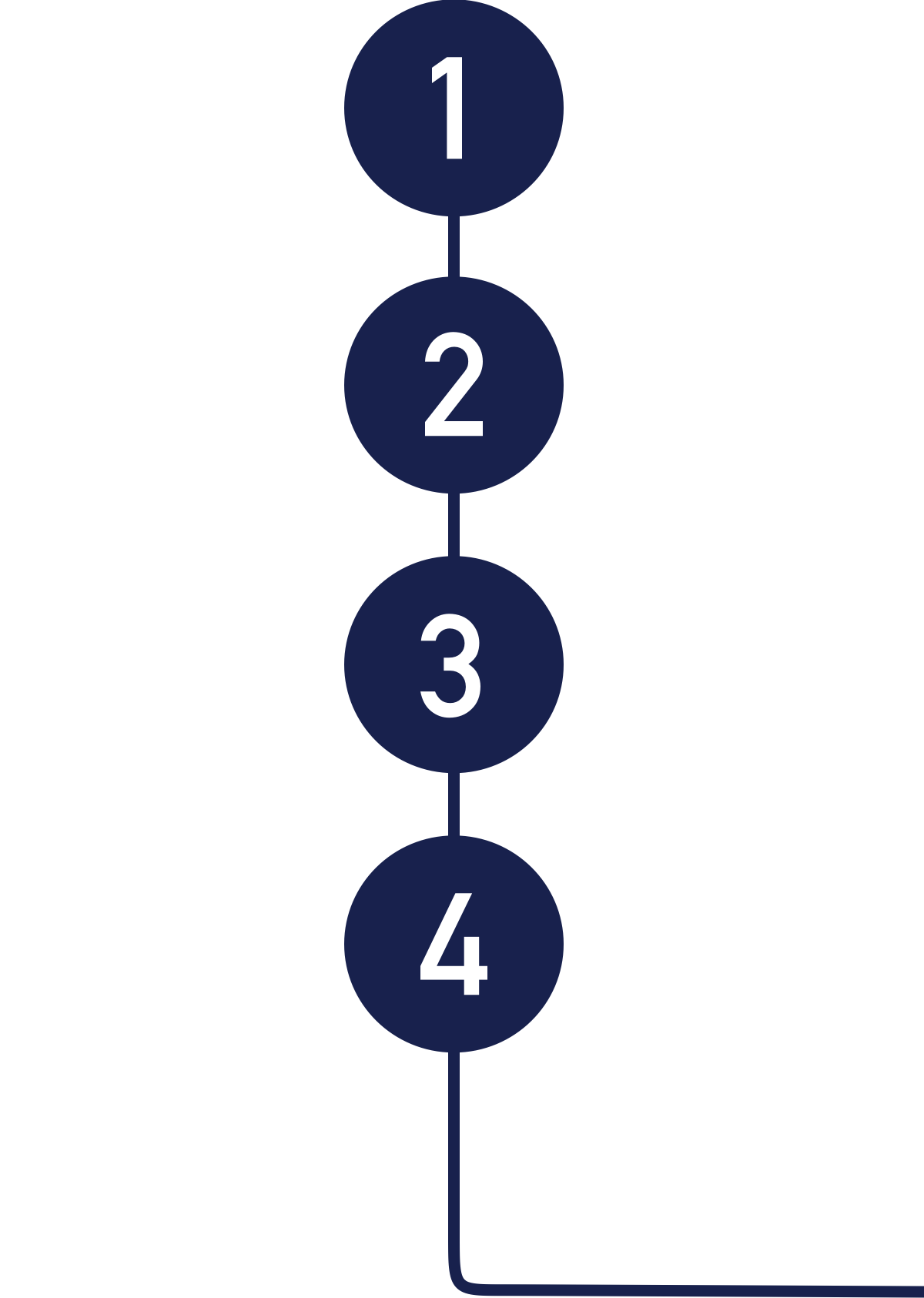
A four-step practical learning strategy with simulated cyberattacks
We consider learning through experience as the way towards mastering any subject. Confronting the danger itself with our phishing simulations will increase the user’s capacity to accurately respond to existing and new cyberattacks. Undergoing the concrete experience followed by reflexion and conceptualization will give your employees valuable decision-making skills.
Simulated Phishing Emails
The first step consists of sending out real-world email simulations. For higher accuracy, the emails are tailored keeping into account your organization’s preferred platforms. Additionally, emailing occurs randomly in order to avoid time patterns. By mindfully taking these aspects into account, we make sure the significance of your employee’s response is high.
Simulated Landing Pages
After taking the bait in an email, users are redirected to a replica of the original landing page, where data breaches usually occur. With a sense of urgency, they are lured into filling in company-related or personal information, such as passwords or credit card numbers.
Simulated Malware and Ransomware
Plugins
Just-in-time learning
A fundamental step in completing the user’s practical training, just-in-time learning comes in the form of attack-aware educational pages with interactive learning materials that help them better identify red flags in phishing emails.
Quizzes
Lastly, the quizzes’ function is to monitor the learning process at the end of every lesson. The results are turned into conclusive reports on your company’s situation.
Practice Makes Perfect
To achieve your desired results, the testing should occur at regular intervals. Avoiding scam emails is a continuous learning process optimal to start as soon as possible, and to maintain for an unlimited period. We’re ready to supply a long term solution of unique emails for your employee’s training needs.

What Are People Saying about our phishing simulations
Automatic phishing simulations keep us on the edge
Thanks to ATTACK Simulator, I can rest assured that I’m doing everything in my power to protect the company security-wise, from the inside out. The platform itself is easy to use and super-helpful – for myself and my colleagues as well. Looking forward to new updates!
My company culture has changed
I didn’t realize how much we needed ATTACK Simulator until we got it. It works on a large array of phishing and malware attack simulations, very realistic ones. I was about to fall into some of those traps myself. But I’m really glad to see employees all over the company doing so less and less.
Our company is seeing positive results
This tool painted a clear picture of where our company was on the topic of cyber-security and it wasn’t pretty. ATTACK Simulator has provided us all with some much-needed knowledge on how to best handle phishing or malware attacks. And it has definitely provided me with some peace of mind.
There’s no reason to postpone training your employees
Get a quote based on your organization’s needs and start building a strong cyber security infrastructure today.
